Hackers Exploited Twitter Bug to Find Linked Phone Numbers of Users
Twitter today issued a warning revealing that attackers abused a legitimate functionality on its platform to unauthorizedly determine phone numbers associated with millions of its users' accounts.
According to Twitter, the vulnerability resided in one of the APIs that has been designed to make it easier for users to find people they may already know on Twitter by matching phone numbers saved in their contacts with twitter accounts.
To be noted, the feature worked precisely as intended, except someone was not supposed to upload millions of randomly generated phone numbers and abuse Twitter to reveal profiles associated with the contact information users added to Twitter for enabling security features.
Though the company is not sure if the bug was exploited by only a single adversary or multiple groups, it has identified several accounts engaged in the attack located in a wide range of countries, primarily from Iran, Israel, and Malaysia.
Based on their IP addresses, Twitter believes some of the accounts who exploited the API flaw may have ties to state-sponsored actors; thus, it is "disclosing this [incident] out of an abundance of caution and as a matter of principle."
"We immediately suspended these accounts and are disclosing the details of our investigation to you today because we believe it's important that you are aware of what happened, and how we fixed it," Twitter said in a blog post.
The company became aware of the issue on December 24 last year after a security researcher 'unethically' exploited a similar, or the same, loophole in Twitter to successfully match nearly 17 million phone numbers to their profiles.
Twitter says the social networking site has since then addressed the issue and there is no action required from the users' side.
"After our investigation, we immediately made a number of changes to this endpoint so that it could no longer return specific account names in response to queries," Twitter said.
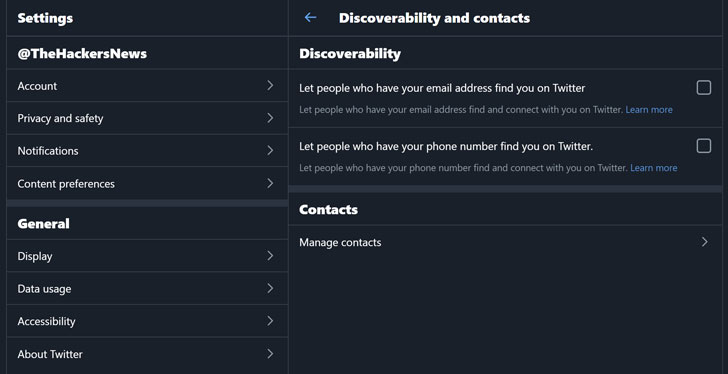
However, if you're unaware, you can also stop anyone from finding your profile based on your email address or phone number by navigating to the 'Discoverability' setting in your Twitter account and disable it.
According to Twitter, the vulnerability resided in one of the APIs that has been designed to make it easier for users to find people they may already know on Twitter by matching phone numbers saved in their contacts with twitter accounts.
To be noted, the feature worked precisely as intended, except someone was not supposed to upload millions of randomly generated phone numbers and abuse Twitter to reveal profiles associated with the contact information users added to Twitter for enabling security features.
Though the company is not sure if the bug was exploited by only a single adversary or multiple groups, it has identified several accounts engaged in the attack located in a wide range of countries, primarily from Iran, Israel, and Malaysia.
Based on their IP addresses, Twitter believes some of the accounts who exploited the API flaw may have ties to state-sponsored actors; thus, it is "disclosing this [incident] out of an abundance of caution and as a matter of principle."
"We immediately suspended these accounts and are disclosing the details of our investigation to you today because we believe it's important that you are aware of what happened, and how we fixed it," Twitter said in a blog post.
The company became aware of the issue on December 24 last year after a security researcher 'unethically' exploited a similar, or the same, loophole in Twitter to successfully match nearly 17 million phone numbers to their profiles.
Twitter says the social networking site has since then addressed the issue and there is no action required from the users' side.
"After our investigation, we immediately made a number of changes to this endpoint so that it could no longer return specific account names in response to queries," Twitter said.
However, if you're unaware, you can also stop anyone from finding your profile based on your email address or phone number by navigating to the 'Discoverability' setting in your Twitter account and disable it.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.