App Used by Israel's Ruling Party Leaked Personal Data of All 6.5 Million Voters
An election campaigning website operated by Likud―the ruling political party of Israeli Prime Minister Benjamin Netanyahu―inadvertently exposed personal information of all 6.5 million eligible Israeli voters on the Internet, just three weeks before the country is going to have a legislative election.
In Israel, all political parties receive personal details of voters before the election, which they can't share with any third party and are responsible for protecting the privacy of their citizens and erasing it after the elections are over.
Reportedly, Likud shared the entire voter registry with Feed-b, a software development company, who then uploaded it a website (elector.co.il) designed to promote the voting management app called 'Elector.'
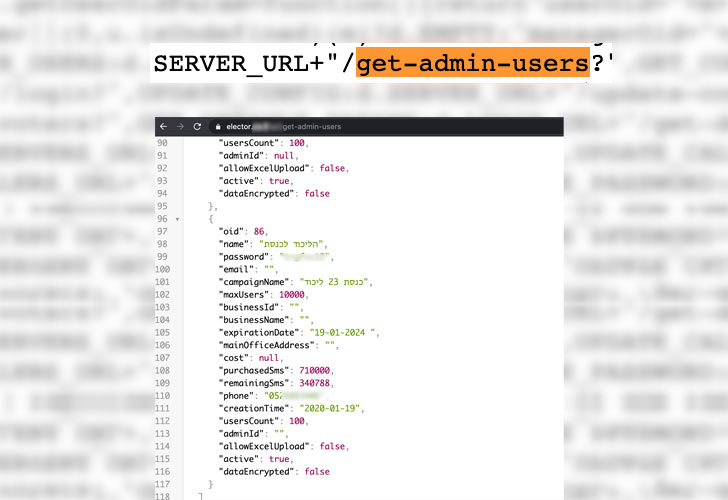
According to Ran Bar-Zik, a web security researcher who disclosed the issue, the voters' data was not leaked using any security vulnerability in the Elector app; instead, the incident occurred due to negligence by the software company who leaked the username and password for the administrative panel through an unprotected API endpoint that was listed in the public source code of its homepage, as shown.
"Someone visiting the Elector website on a standard browser like Google's Chrome could right-click their mouse on the page and select 'View page source.' The revealed source code for the website contained a link to the 'get-admins-users' page, which the prospective hacker simply had to visit in order to find, out in the open, the passwords of "admin" users — those with authorization to manage the database." Israeli media explained.
The exposed database includes the full names, identity card numbers, addresses, and gender of 6,453,254 voters in Israel, as well as the phone numbers, father's name, mother's name, and other personal details of some of them.
Through the affected Elector website is down for many users at the time of writing, some media reports confirm the software company has now patched the issue but can't ensure how many people have since then been able to download the voters' database.
The Israeli Justice Ministry's Privacy Protection Authority (PPA) said it was investigating the incident.
In Israel, all political parties receive personal details of voters before the election, which they can't share with any third party and are responsible for protecting the privacy of their citizens and erasing it after the elections are over.
Reportedly, Likud shared the entire voter registry with Feed-b, a software development company, who then uploaded it a website (elector.co.il) designed to promote the voting management app called 'Elector.'
According to Ran Bar-Zik, a web security researcher who disclosed the issue, the voters' data was not leaked using any security vulnerability in the Elector app; instead, the incident occurred due to negligence by the software company who leaked the username and password for the administrative panel through an unprotected API endpoint that was listed in the public source code of its homepage, as shown.
"Someone visiting the Elector website on a standard browser like Google's Chrome could right-click their mouse on the page and select 'View page source.' The revealed source code for the website contained a link to the 'get-admins-users' page, which the prospective hacker simply had to visit in order to find, out in the open, the passwords of "admin" users — those with authorization to manage the database." Israeli media explained.
The exposed database includes the full names, identity card numbers, addresses, and gender of 6,453,254 voters in Israel, as well as the phone numbers, father's name, mother's name, and other personal details of some of them.
Through the affected Elector website is down for many users at the time of writing, some media reports confirm the software company has now patched the issue but can't ensure how many people have since then been able to download the voters' database.
The Israeli Justice Ministry's Privacy Protection Authority (PPA) said it was investigating the incident.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.