Source Code for CARBANAK Banking Malware Found On VirusTotal
Security researchers have discovered the full source code of the Carbanak malware—yes, this time it's for real.
Carbanak—sometimes referred as FIN7, Anunak or Cobalt—is one of the most full-featured, dangerous malware that belongs to an APT-style cybercriminal group involved in several attacks against banks, financial institutions, hospitals, and restaurants.
In July last year, there was a rumor that the source code of Carbanak was leaked to the public, but researchers at Kaspersky Lab later confirmed that the leaked code was not the Carbanak Trojan.
Now cybersecurity researchers from FireEye revealed that they found Carbanak's source code, builders, and some previously unseen plugins in two RAR archives [1, 2] that were uploaded on the VirusTotal malware scanning engine two years ago from a Russian IP address.
FireEye researchers have plans to release a 4-part series of articles detailing CARBANAK features and analysis based upon its source code and reverse engineering.
First uncovered in 2014 by Kaspersky Lab, Carbanak is one of the most successful malware attacks in the world launched by a highly organized group that continually evolved its tactics to carry out cybercrime while avoiding detection by potential targets and the authorities.
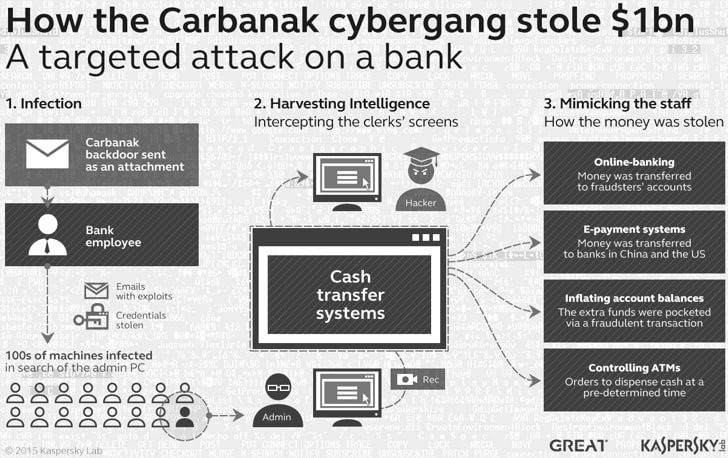
The hacker group started its activities almost six years ago by launching a series of malware attacks using Anunak and Carbanak to compromise banks and ATM networks worldwide, and thereby stealing over a billion euros from more than 100 banks across the globe.
To compromise banks, hackers sent malicious spear-phishing emails to hundreds of employees at different banks, which infected computers with Carbanak malware if opened, allowing attackers to transfer money from affected banks to fake accounts or ATMs monitored by them.
According to the European authorities, the criminal group later developed a sophisticated heist-ready banking trojan called Cobalt, based on the Cobalt-Strike penetration testing software, which was in use until 2016.
The group was first exposed in 2015 as financially-motivated cybercriminals, and three suspects—Dmytro Fedorov, 44, Fedir Hladyr, 33, and Andrii Kopakov, 30—all from Ukraine were arrested last year in Europe between January and June.
All the three suspects, one of which (Kopakov) is believed to be the alleged leader of the organised criminal group, were indicted and charged with a total of 26 felony counts in August 2018.
Carbanak—sometimes referred as FIN7, Anunak or Cobalt—is one of the most full-featured, dangerous malware that belongs to an APT-style cybercriminal group involved in several attacks against banks, financial institutions, hospitals, and restaurants.
In July last year, there was a rumor that the source code of Carbanak was leaked to the public, but researchers at Kaspersky Lab later confirmed that the leaked code was not the Carbanak Trojan.
Now cybersecurity researchers from FireEye revealed that they found Carbanak's source code, builders, and some previously unseen plugins in two RAR archives [1, 2] that were uploaded on the VirusTotal malware scanning engine two years ago from a Russian IP address.
"CARBANAK source code was 20MB comprising 755 files, with 39 binaries and 100,000 lines of code," researchers say. "Our goal was to find threat intelligence we missed in our previous analyses."
FireEye researchers have plans to release a 4-part series of articles detailing CARBANAK features and analysis based upon its source code and reverse engineering.
First uncovered in 2014 by Kaspersky Lab, Carbanak is one of the most successful malware attacks in the world launched by a highly organized group that continually evolved its tactics to carry out cybercrime while avoiding detection by potential targets and the authorities.
The hacker group started its activities almost six years ago by launching a series of malware attacks using Anunak and Carbanak to compromise banks and ATM networks worldwide, and thereby stealing over a billion euros from more than 100 banks across the globe.
To compromise banks, hackers sent malicious spear-phishing emails to hundreds of employees at different banks, which infected computers with Carbanak malware if opened, allowing attackers to transfer money from affected banks to fake accounts or ATMs monitored by them.
According to the European authorities, the criminal group later developed a sophisticated heist-ready banking trojan called Cobalt, based on the Cobalt-Strike penetration testing software, which was in use until 2016.
The group was first exposed in 2015 as financially-motivated cybercriminals, and three suspects—Dmytro Fedorov, 44, Fedir Hladyr, 33, and Andrii Kopakov, 30—all from Ukraine were arrested last year in Europe between January and June.
All the three suspects, one of which (Kopakov) is believed to be the alleged leader of the organised criminal group, were indicted and charged with a total of 26 felony counts in August 2018.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.